Best Network Protection
Introduction
The Network Protection now that’s a topic that really gets my gears grinding. As someone who’s been elbow-deep in the cybersecurity industry for longer than I care to admit I’ve seen my fair share of businesses and individuals struggle to keep their digital defenses up to par. And let me tell you, it’s not for lack of trying. Nope, the problem is that the world of network security is a minefield of confusing jargon ever changing threats, and oh-so-many “solutions” that promise the moon but deliver…well, let’s just say, less than stellar results.
But fear not, my friends, because I’m here to cut through all the noise and give you the real scoop on the best network protection out there. You see, in this day and age, having a robust and proactive security posture isn’t just a “nice-to-have” it’s an absolute necessity. We’re talking about everything from data breaches and ransomware attacks to good old-fashioned industrial espionage. And trust me, the cybercriminals out there? They’re getting more sophisticated by the day.
So, if you’re looking to keep your network and by extension your business or personal assets – safe from the clutches of the digital underworld, you need to be armed with the right knowledge and tools. And that’s exactly what I’m here to provide. Buckle up, folks, because we’re about to dive deep into the world of best-in-class network protection.
What Exactly is Best Network Protection, and Why is it so Important?
what do you mean by ‘Best Network Protection,’ and why should I even care?” Well, let me break it down for you:
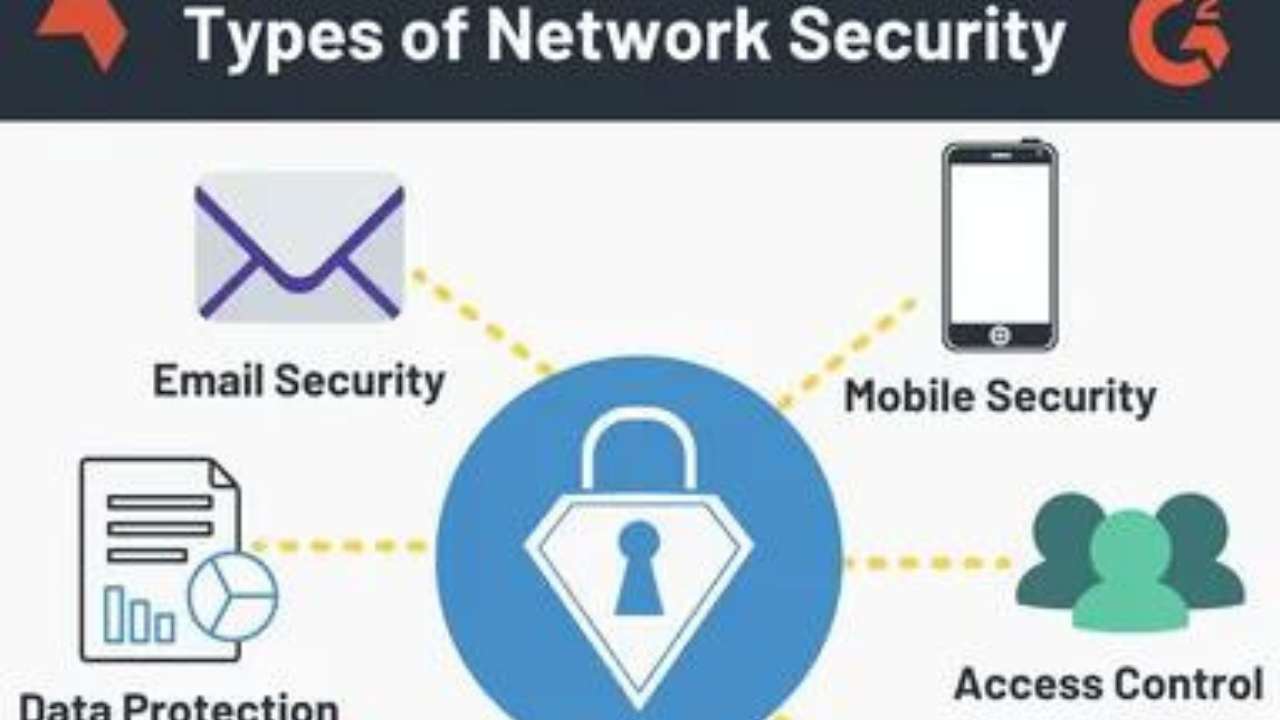
Network protection refers to the comprehensive set of security measures and technologies that are designed to safeguard your digital infrastructure – that’s everything from your wired and wireless networks to your connected devices and online services. It’s the first line of defense against a wide range of cyber threats, from malware and phishing attacks to unauthorized access and data breaches.
And why is it so important, you ask? Well in a world where our lives and livelihoods are increasingly dependent on digital connections, the consequences of poor Network Protection can be devastating. We’re talking about everything from lost productivity and financial losses to irreparable damage to your reputation and even legal repercussions.
Think about it – if your network is compromised, it’s not just your precious data that’s at risk. Nope, the entire ecosystem of connected devices, cloud services, and online interactions that your business (or personal life) relies on could come crashing down. And trust me, you do not want to be the one responsible for that kind of digital disaster.
What are the Key Elements of Effective Network Protection?
Alright, now that we’ve established why network protection is so crucial, let’s talk about the how, shall we? What are the key elements that make up a robust and comprehensive security posture?
1. Firewalls: The foundation of any good network protection strategy, firewalls act as the gatekeepers, controlling the flow of traffic in and out of your network and blocking any unauthorized or suspicious activity.
2. Antivirus and Anti-Malware: These security tools are your first line of defense against malicious software that could infiltrate your network and wreak havoc. They’re constantly on the lookout for known threats and can help detect and neutralize them before they cause any real damage.
3. Virtual Private Networks (VPNs): When it comes to securing your remote and mobile connections, a reliable VPN is an absolute must. It creates an encrypted “tunnel” between your device and the network, shielding your data from prying eyes and preventing unauthorized access.*
4. Network Monitoring and Intrusion Detection: To proactively identify and respond to potential threats, you need robust network monitoring and intrusion detection capabilities. These solutions can alert you to suspicious activity in real-time and help you investigate and mitigate any incidents.
5. Regular Software Updates and Patches: Keeping your network’s software and firmware up-to-date is crucial for plugging security vulnerabilities and staying ahead of the bad guys. It’s a simple but often overlooked aspect of effective network protection.
FAQs About Best Network Protection
Q: What are the most common network security threats that businesses and individuals face?
A: Some of the most prevalent network security threats include malware (such as viruses, worms, and ransomware), phishing and social engineering attacks, DDoS (distributed denial-of-service) attacks, unauthorized access to sensitive data, and insider threats from disgruntled or negligent employees. Staying vigilant and implementing comprehensive security measures is crucial to mitigate these risks.
Q: How can I ensure that my network is properly protected?
A: To ensure effective network protection, it’s important to take a multilayered approach that combines various security technologies and best practices. This includes installing and regularly updating firewalls, antivirus/anti-malware software, virtual private networks (VPNs), and network monitoring/intrusion detection systems. It’s also crucial to keep your software and firmware up-to-date, train your employees on security awareness, and regularly review and test your security posture.
Q: What are the key factors to consider when choosing a network security solution?
A: When selecting a network security solution, some of the key factors to consider include the comprehensiveness of the offering (covering firewalls, antivirus, VPN, etc.), the reliability and performance of the technology, the ease of deployment and management, the flexibility to adapt to your changing needs, the level of support and responsiveness of the provider, and of course, the cost-effectiveness of the solution.
Q: How can I stay informed about the latest network security threats and best practices?
A: To stay up-to-date on the ever-evolving world of network security threats and best practices, it’s important to regularly consult trusted industry resources, such as cybersecurity news websites, industry publications, and expert blogs. You can also subscribe to security alert services, attend relevant webinars and conferences, and network with other security professionals to share knowledge and stay ahead of the curve.
Conclusion
Whew, that was a wild ride, wasn’t it? But hey, when it comes to the world of network security, you’ve got to be ready for the unexpected am I right?
Look, I know it can be a lot to take in all these technical terms, complicated protocols, and ever changing threats. But trust me, in this day and age, effective network protection isn’t just an “IT problem” it’s everyone’s problem. And if you’re not taking the necessary steps to fortify your digital defenses, well, you might as well just hand the keys to your kingdom over to the hackers on a silver platter.
That’s why I put together this comprehensive guide to the best network protection strategies and solutions. From the foundational elements like firewalls and antivirus software to the cutting-edge technologies like VPNs and network monitoring, I’ve tried to give you a well-rounded understanding of what it takes to bulletproof your digital infrastructure.
Because in a world where cybercrime is becoming more sophisticated by the day, having a robust and proactive network security posture is crucial. The consequences of dropping the ball? Yikes we’re talking about everything from data breaches and system downtime to irreparable damage to your (or your organization’s) reputation. And trust me, that’s not something you want to be dealing with.
So, my fellow security-conscious readers, take a long, hard look at this guide. Educate yourself, implement the right solutions, and stay vigilant. Because in the high-stakes world of network protection, the only way to come out on top is to be the best of the best.
After all, in a landscape that’s constantly evolving, the true security superstars are the ones who can adapt, innovate, and stay ahead of the curve. And that’s exactly the kind of proactive and comprehensive approach that I’ve laid out for you here. So, what are you waiting for?